The reality of enterprise IT landscapes is hybrid. On-premise and cloud systems exist in parallel and must be seamlessly connected. For the management of authorizations, a hybrid system landscape means a certain challenge. From day one in the company, every employee should be able to securely access exactly the applications they need to perform their job. This is ensured by a functioning user lifecycle management. However, the assignment of authorizations does not just play a role in smooth processes within the company, but also makes an important contribution to security.
Do you want more ideas for your user lifecycle management in hybrid landscapes?
Multiple threats to IT security
The threat situation in terms of cyber security has changed: While companies used to be exposed to more random attacks, frequent and targeted attacks on IT infrastructures are now commonplace. The dangers range from malware such as viruses and trojans, to phishing attacks to spy on access data or other information, to ransomware, which makes companies vulnerable to blackmail by encrypting data. In addition, data leaks are also becoming known time and again.
Software security vulnerabilities often act as a gateway for cyber criminals. Working from a home office, which has gone from being the exception to the rule in many industries as a result of the Corona pandemic, offers hackers another point of attack. Therefore, the task for companies is to provide their employees with secure access to the IT systems they need, even remotely. The prerequisite for this: the clean assignment of roles and authorizations.
Employees need appropriate authorizations
The process of user lifecycle management starts when an employee joins the company. The HR department creates the new employee’s data, which is then loaded into SAP Identity Management (IdM). Based on his or her job, the user is assigned a business role that is linked to various basic accounts.
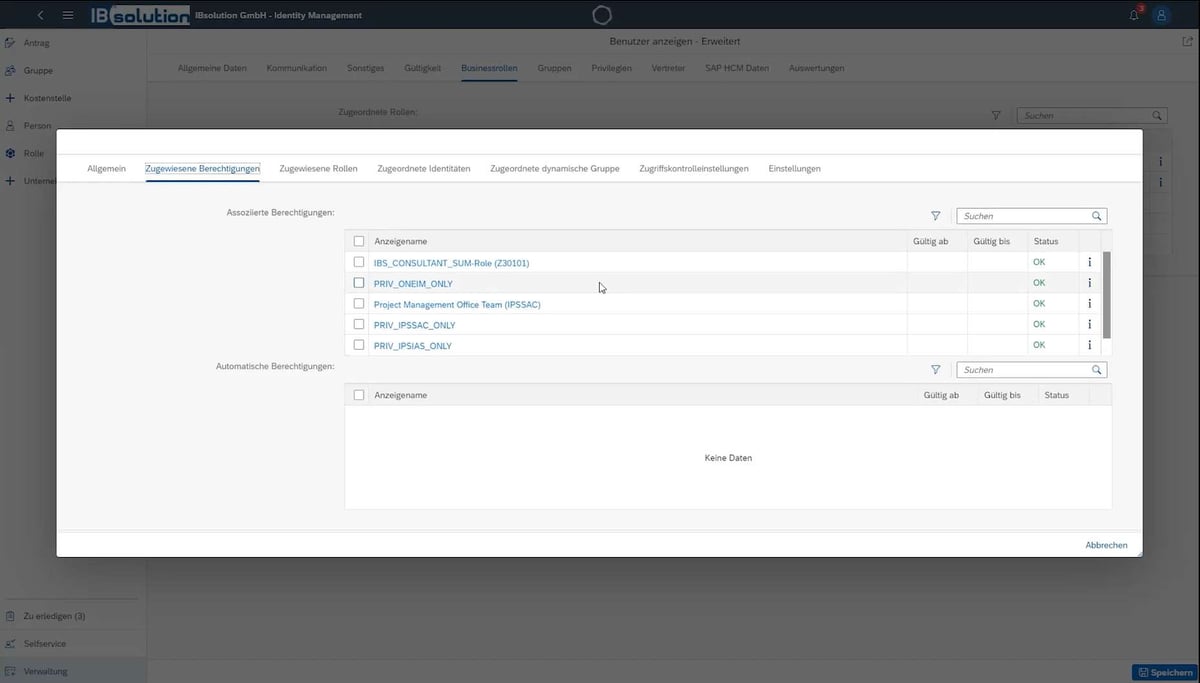
SAP Identity Management is connected to the target systems via connectors and provisions the data so that the employee has access to the systems and the corresponding authorizations – not only for SAP systems – are distributed. Provisioning in the cloud systems takes place via special services, for example the SAP Identity Provisioning Service (IPS).
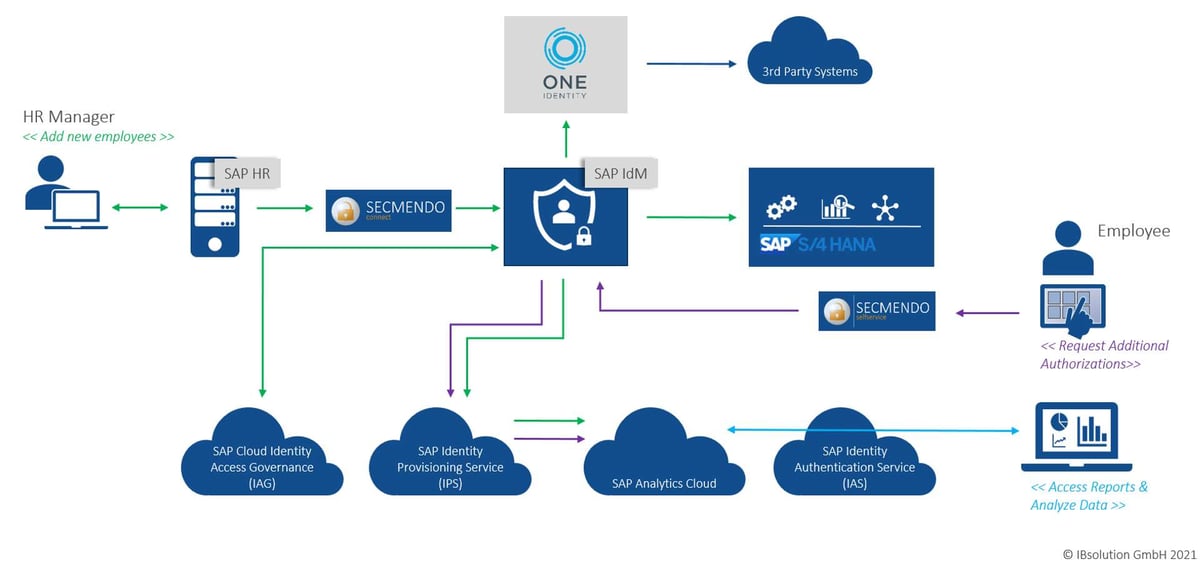
To achieve a high degree of automation for authorizations, as many systems as possible are linked to the employee’s job description. This speeds up processes and increases the efficiency of user lifecycle management. At the same time, the fact that employees only receive authorizations for those systems that they actually need to carry out their work makes an important contribution to cyber security. If the employee changes jobs or departments within the company, the authorizations must be adjusted accordingly.
Business and technical review
Authorizations that go beyond the basic accounts and are required for management activities, for example, must be applied for separately. With the help of self-service functionalities, the employee can do this independently and the process can be handled completely paperless. In the first instance, the supervisor approves the requested authorizations.
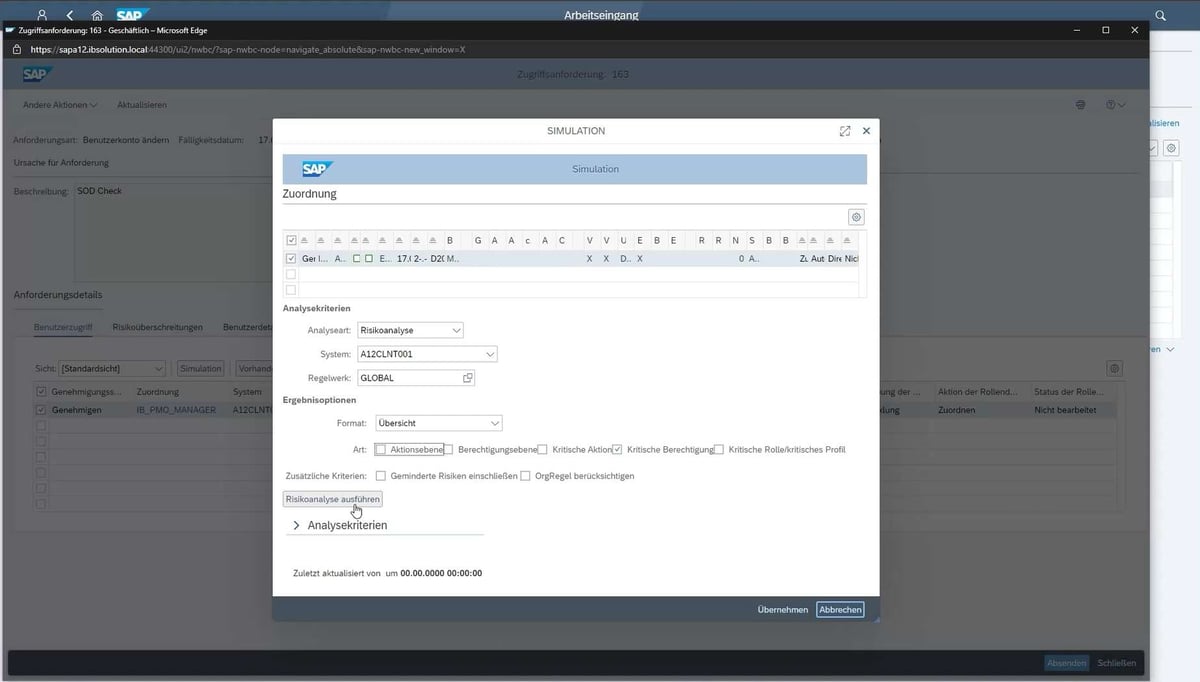
However, the combination of different authorizations can lead to conflicts, which is why an SoD (Segregation of Duties) check is always required. This segregation of duties prevents an employee from being able to fraudulently run through an entire business process on his or her own. The SoD check takes place in SAP Access Control. The software presents the access requests from SAP Identity Management, whereupon the role owner checks and releases the critical authorizations if there is no violation of the separation of functions. If conflicts arise in the authorizations, mitigation, for example by SAP Access Control, must limit the risk. Only conflict-free authorizations ensure maximum security in business processes.
Ideally prepared for audits
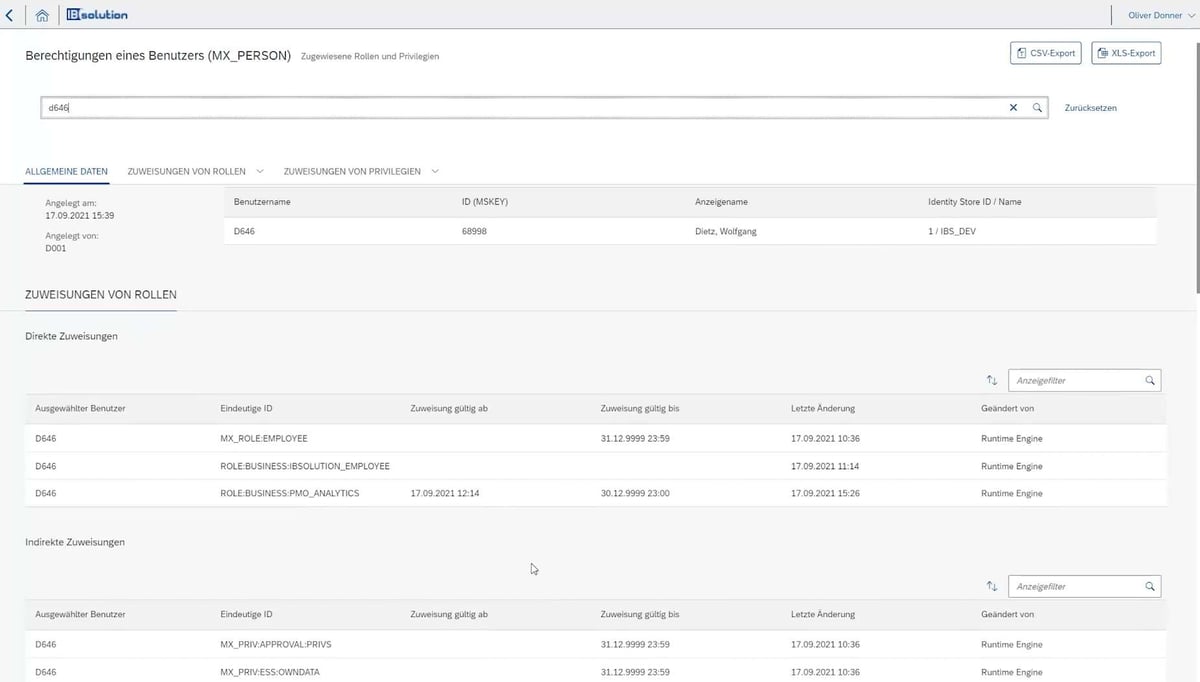
Traceability in roles and authorizations as well as complete process documentation are important topics with regard to IT security and also relevant for audits. In order to be able to access historical data in SAP Identity Management quickly and easily during audits, for example, there are helpful tools such as SECMENDO.report. Their use saves a lot of time when creating reports for the auditor. At the same time, IdM administrators are able to get an overview of the roles and authorizations in the company.
With SECMENDO.authority_audit, the assigned ABAP roles and authorizations can be analyzed and compared centrally in a dashboard in SAP Analytics Cloud. The Live Data Connection to the target system enables administrators to retrieve the information on roles, authorizations and users in real time. The comparison of users on the basis of job-related HR data quickly and easily reveals inconsistencies in the assignment of authorizations.
If it turns out that an employee has access to a certain application but is not using it, it can make sense to revoke this authorization. On the one hand, this has a positive effect on costs if licenses can be saved as a result. On the other hand, an unused account always represents a security risk and offers cyber criminals a welcome gateway.
Manage the entire identity lifecycle
This example once again illustrates the importance of holistic user lifecycle management. It is not only relevant when an employee joins or leaves the company, but spans the entire lifecycle of identities – from creation to management to restriction and termination of access to data, systems and applications.
![IBacademy_Logo_blau[496] IBacademy_Logo_blau[496]](https://www.ibsolution.com/hs-fs/hubfs/IBacademy_Logo_blau%5B496%5D.jpg?width=200&name=IBacademy_Logo_blau%5B496%5D.jpg)




