SAP Access Control and SAP Cloud Identity Access Governance (IAG) address the management of users and authorizations in compliance with rules and with as little risk as possible. While SAP Access Control is an on-premise solution, SAP IAG is available as a cloud service on SAP Business Technology Platform. In terms of functionalities, what are the similarities and differences between the two solutions?
Do you want to distribute, manage and check roles and users in the cloud?
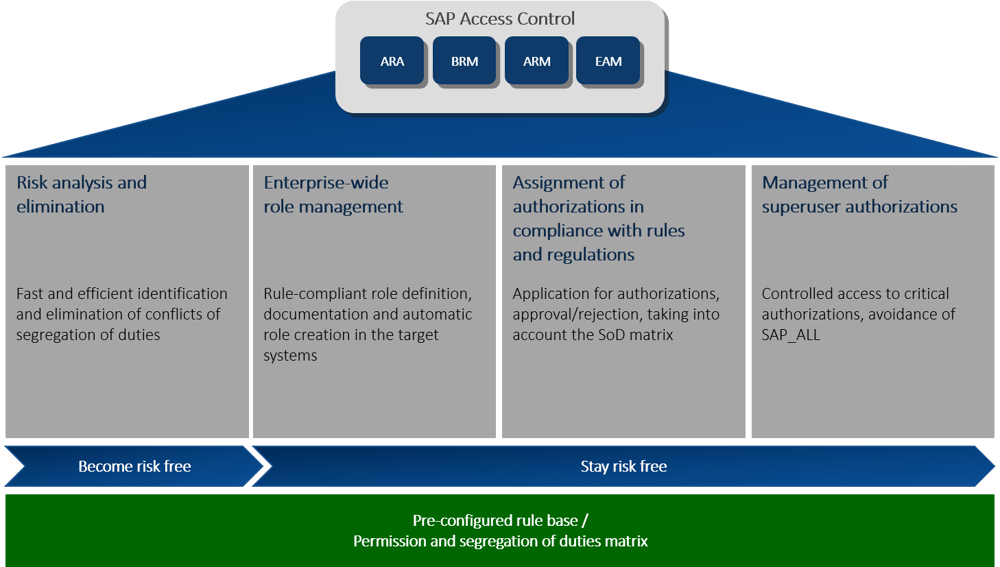
Four modules for risk prevention
Both SAP Access Control and SAP IAG consist of four modules:
-
Risk analysis and elimination (fast and efficient identification and elimination of segregation of duties conflicts).
-
Enterprise-wide role management (rule-compliant role definition, documentation and automatic role creation in the target systems)
-
Rule- and law-compliant assignment of authorizations (application for authorizations, approval or rejection taking into account the SoD matrix)
-
Management of superuser authorizations (controlled access to critical authorizations while avoiding SAP_ALL)
With these four modules, both solutions enable continuous risk prevention through role management. While the Risk Analysis and Elimination module is designed to help organizations become risk-free, the other three modules ensure that they remain risk-free.
Risk analysis
With SAP Access Control, risk analyses can be performed on an ad hoc basis at the role and user level or as part of an application process. In addition, functionalities for simulations are also available. Risk mitigations can be performed – based on rules – as part of mitigations. The analysis of risks is already possible in the role development (Business Role Management, BRM), so that risk-free roles can be created.
SAP IAG enables risk analysis at the role and user level – also ad hoc or as part of an application process. One IAG functionality that SAP Access Control does not offer is access refinement. This allows access to be refined based on suggestions from the system, and automatic role revocation can be performed based on the use of authorizations and roles.
Role management
SAP Access Control enables central management of roles – from definition, creation and modification to distribution to the connected target systems. Role management can be performed on a process-related basis. The creation and modification of roles can be directly linked to a check for risks. This provides assurance that roles are risk-free or at least low-risk from the outset.
As far as business role management is concerned, there are no significant differences between SAP Access Control and SAP IAG. SAP Access Control offers the possibility to develop SAP roles – in addition to business roles. SAP IAG offers additional features with regard to automation and intelligence. This includes, for example, a check for overlap with other roles. The system also provides an overview of the coverage and use of business roles: How often do which users use which roles?
Application and assignment processes
With SAP Access Control, users can carry out application processes for themselves (self-service), for other users, for new users, and for changes to existing users. As part of the application process, a check is performed to determine whether new risks arise when authorizations change, and what effects this may have. In addition, a request for superuser access can be made from the Emergency Access Management (EAM) module to enable emergency actions to be taken. The workflow engine of SAP Access Control contains predefined processes and rules based on BRF+ and MSMP. These processes and rules are flexibly customizable so that more complex scenarios with multiple release instances can be mapped.
SAP IAG offers fewer options than SAP Access Control in terms of request and approval processes. The scope of functions includes initiating request processes as self-service, for other users and for making changes to existing users. Likewise, a request for access by a superuser is also possible. However, it lacks such a powerful workflow engine as SAP Access Control offers. The corresponding workflow from SAP IAG is rather straightforward and has fewer options for configuration and less flexibility in implementing processes.
Emergency Access Management (EAM)
SAP Access Control provides process-oriented superusers without the use of SAP_ALL. Appropriate logging helps to keep track of what has happened. The recommendation is to set up superusers for various scenarios from the business departments.
Emergency Access Management is called Privileged Access Management (PAM) at SAP IAG. Apart from the name, however, there are no differences between this module and SAP Access Control. The identical functionalities are available for firefighter processes.
Conclusion: Both solutions with comparable features
A key differentiator between SAP Access Control and SAP IAG is the architecture: SAP Access Control is an on-premise solution, while SAP IAG is sourced from the cloud – with the corresponding consequences in terms of availability, maintenance and hardware. SAP provides new releases for SAP IAG every quarter.
In terms of functionality, the two solutions are congruent in many respects. The differences lie more in the details. One of the strengths of SAP Access Control is the flexible workflow design for application procedures. SAP IAG enables direct checking of SAP cloud applications, but can also be used for on-premise systems such as SAP ERP or SAP S/4HANA using SAP Cloud Connector. Non-SAP systems can be connected via an SCIM interface. SAP IAG’s Access Certification Campaign offers the ability to run campaigns with a defined target and output.
Is there a better choice?
If companies are faced with the decision to introduce one of the two solutions, various factors play a role, such as the existing system landscape and the company’s general IT strategy. If cloud applications are already available in addition to on-premise systems, the recommendation is more in the direction of SAP IAG. This allows hybrid scenarios to be integrated in the best possible way. Those who already use SAP Access Control should consider a bridge scenario: SAP IAG is also integrated into the system landscape so that both solutions handle authorization management together.
![IBacademy_Logo_blau[496] IBacademy_Logo_blau[496]](https://www.ibsolution.com/hs-fs/hubfs/IBacademy_Logo_blau%5B496%5D.jpg?width=200&name=IBacademy_Logo_blau%5B496%5D.jpg)




