With the IT Security Act 2.0, which came into force on May 1, 2023, the legislator in Germany has created a stricter regulation for critical infrastructures (KRITIS). Non-compliance with it will result in severe sanctions. The reason for this new legal provision on the IT security of CRITIS companies was not least the enormous number of cyber attacks, which had once again skyrocketed, especially with the home office obligation during the Corona pandemic. The threat potential for companies remains as high as ever and is even increasing.
Learn everything you need to know about NIS 2
EU-wide standard for cyber security
What follows from this: Cyber security must not be a luxury, but must become the standard, the stable basis of every company. In the meantime, the European Union has created the framework for a new standard that is intended to better protect the globally operating European economy from cyber attacks: Building on the first NIS (Network and Information Security) version of 2016, NIS 2 came into force on January 16, 2023 as the new EU cyber security directive. The EU member states have until October 18, 2024 to transpose the provisions of NIS 2 into national law. For Germany, a first draft of the IT Security Act 3.0 is expected soon.
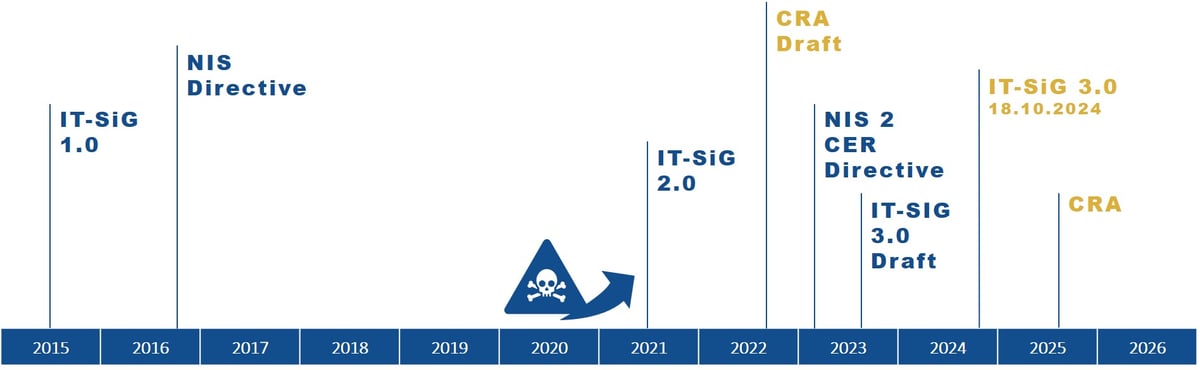
The various legislative initiatives for higher cyber security over time.
NIS 2 affects significantly more companies
The scope of NIS 2 has been significantly expanded: The directive already applies to companies with a size of 50 employees and a turnover of 10 million euros. This means that an estimated 40,000 additional companies are affected across the EU. For the first time, a distinction is made between entities in the “Essential” and “Important” categories, some of which differ in terms of requirements. Sectors with high criticality include energy, transport, banks, financial markets and digital infrastructures. Public administration is also explicitly mentioned. The category of other critical sectors includes, for example, postal and courier services, providers of digital services, but also manufacturers of medical devices and mechanical and vehicle engineering.
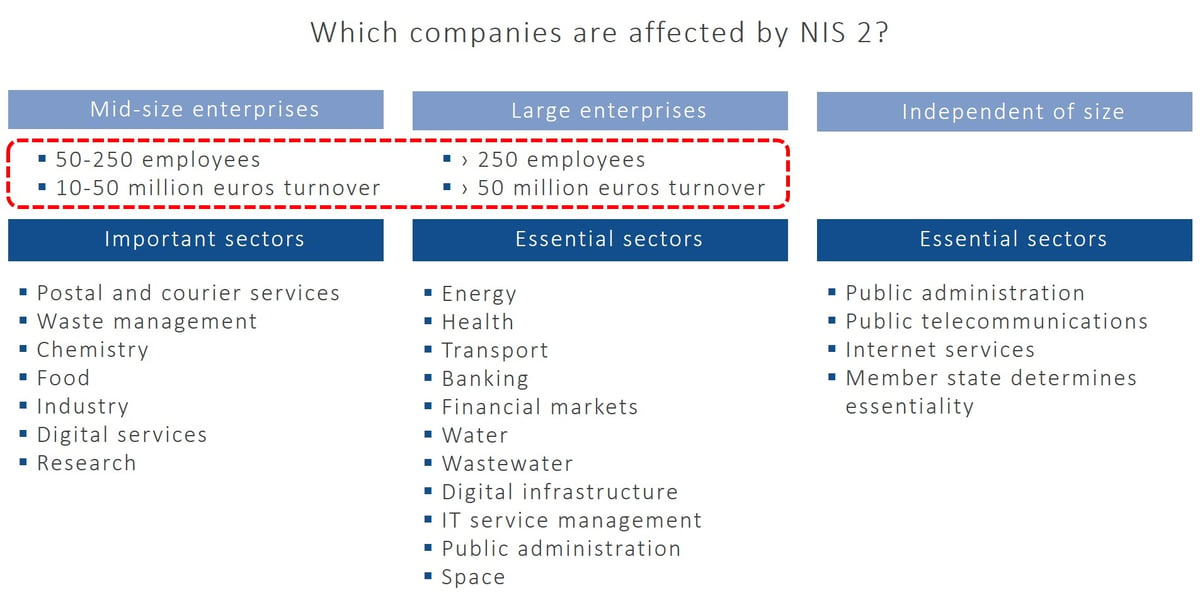
Mid-sized and large KRITIS companies fall within the scope of NIS 2. For certain industries, NIS 2 applies regardless of company size.
Violations of NIS 2 are subject to severe penalties, which are similar in scope to the General Data Protection Regulation (GDPR). The fines due can amount to up to 10 million euros or 2% of annual sales. The liability extension is also particularly worth mentioning: with NIS 2, cyber security becomes an integral part of corporate management, as management can be held liable in the event of violations.
The most important provisions of NIS 2
The European NIS 2 directive already contains key provisions that will later also be found in the German IT Security Act 3.0. Even if there are still uncertainties regarding the actual wording of the liability issue in the law, other provisions of NIS 2 will be elementary components of the IT Security Act 3.0.
Among other things, companies must develop a risk management concept and introduce emergency plans. In addition, a system for the rapid reporting of incidents to the responsible supervisory authority is prescribed so that rapid warnings can also be published for other companies. NIS 2 also obliges companies to develop protection concepts for securing their supply chains so that cyber criminals cannot penetrate other companies’ systems via suppliers. This is a very sensible regulation, as this is precisely the case that has often occurred in the past. Securing supply chains can usually only be ensured or verified via security frameworks such as ISO 27001 certification.
Extended powers of the authorities
Mandated technical measures include systematic data backups, access control concepts, information encryption, vulnerability management and employee training. NIS 2 also expands the powers and courses of action available to national competent authorities. According to the drafted law, the German Federal Office for Information Security (BSI) will in future even be able to temporarily prohibit people “who, as management or legal representatives, are responsible for management tasks at the particularly important facility from performing management tasks” if they fail to comply with the BSI’s orders.
What is the best way for companies to proceed?
In order to comply with the provisions of NIS 2 in the future, companies that fall within the scope of the EU directive should first ask themselves the following questions: Where do we stand in terms of cyber security? How secure are our SAP systems currently? A suitable starting point is our “360 Degree Security Check for SAP Landscapes”, which is designed as a two-day workshop and covers the current state of IT security across all relevant layers.
The topic of threat detection is already anchored in the IT Security Act 2.0. Performing the threat detection manually is impossible, so companies need to establish appropriate tools. SAP Enterprise Threat Detection (ETD), as a cloud solution, provides a solid basis for SAP security monitoring.
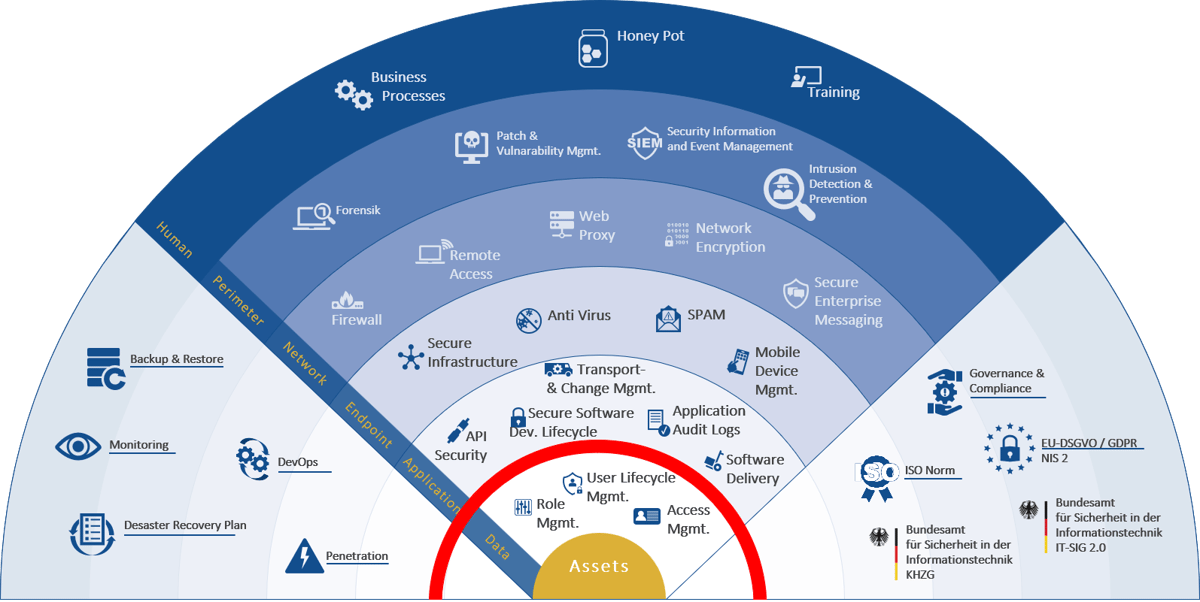 Role management, access management and user lifecycle management significantly increase the level of security in the data layer.
Role management, access management and user lifecycle management significantly increase the level of security in the data layer.
Roles and access as decisive factors
Governance and compliance are among the main pillars of the NIS 2 directive and address role management, access management and user life cycle management. This involves questions of authorization and authentication as well as appropriate permissions. The authorization concepts, most of which are getting on in years, must be redesigned in order to realize the goal of business roles. This is the only way to automate the assignment of authorizations and ensure rapid intervention.
Access management currently offers the greatest leverage for IT security in the context of implementation. Without multi-factor authentication (MFA), companies are much more vulnerable to phishing attacks. Identity management with single sign-on and MFA is not a luxury, but an indispensable requirement for the management and control of identities, accesses and authorizations. Or how would you implement an ad hoc password reset across all accounts and systems if your IT infrastructure was compromised?
![IBacademy_Logo_blau[496] IBacademy_Logo_blau[496]](https://www.ibsolution.com/hs-fs/hubfs/IBacademy_Logo_blau%5B496%5D.jpg?width=200&name=IBacademy_Logo_blau%5B496%5D.jpg)







