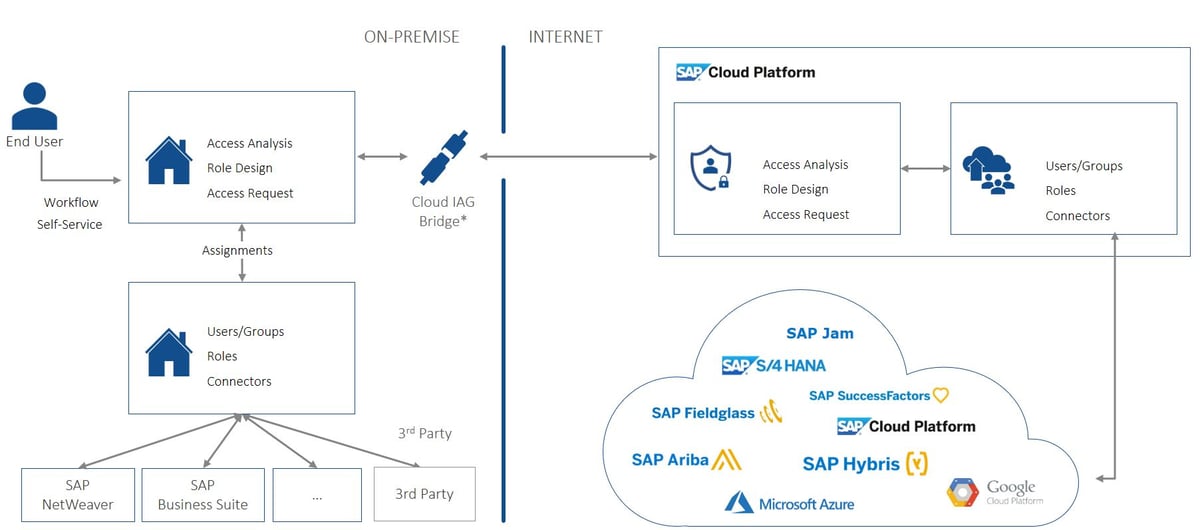
SAP Cloud Identity Access Governance (IAG) is the cloud counterpart to SAP Access Control, which is bundled with SAP cloud products. The identity management and access control processes of the user lifecycle are moved to the cloud to specifically manage cloud systems (but also on-premise systems).
In conjunction with SAP Identity Provisioning (IPS) and SAP Identity Authentication (IAS), employee onboarding and offboarding processes are mapped in a fully comprehensive user lifecycle. Rules can be created and analyses performed to avoid access risks and conflicts of interest (SoD). As with SAP Access Control, it is possible to perform and monitor mitigations when rule violations are detected for access requests.
Using SAP IAS, end-to-end authentication via single sign-on (SSO) is achieved to provide users with an efficient and convenient way of working without media disruption.
SAP Cloud Identity solutions enable authentication (IAS), single sign-on (SSO) and provisioning (IPS) against SAP cloud systems. SAP Cloud Identity Access Governance (IAG) provides the ability to manage workflows, risk checks and emergency access. Especially in a hybrid system landscape and in the communication between on-premise and cloud systems, the products ensure complete integration.
SAP Cloud Identity Access Governance (IAG)

SAP Identity Management focuses on the traceable management and consistent distribution of digital identities throughout their lifecycle – assignment, repeated adjustments, deletion. The SAP IdM solution makes it possible to flexibly map individual workflows so that required user accounts, roles, and authorizations can be assigned in a rule-based and automated manner.

Single sign-on enables end-to-end authentication against SAP and non-SAP applications. Central management of access data increases security, as only one user ID is required for all applications. This means that passwords can be made truly secure without restricting user convenience too much. Constantly changing passwords for each application is a thing of the past, and password resets are minimized. You also avoid duplicate administration efforts in your IT and free up valuable resources.

You would like to newly implement SAP Access Control, SAP Cloud Identity Access Governance or SAP Identity Management (IdM) or extend your existing system? With our Power Workshop for SAP Access Governance, you benefit from de facto standards that we adapt step by step to your individual requirements. As a result, you will receive a recommended action with a suitable project plan for introducing the access governance product that is optimal for you.
Especially in a hybrid system landscape with cloud and on-premise systems as well as non-SAP software such as Microsoft Azure, a continuous identity lifecycle is mandatory. Clear monitoring and audits are possible at any time via Fiori Launchpad to ensure the security of the systems. In conjunction with SAP Identity Management and/or SAP Access Control, the entire hybrid system landscape can be covered according to company-specific compliance requirements. Synchronization between the systems enables constant data storage and cross-platform administration.
|
|

Integrate SAP Cloud Identity Access Governance into your system landscape to extend user and authorization management and risk assessment to your cloud systems.

Automate your identity management processes in the cloud. Use the new SAP Cloud Identity Services (Identity Provisioning and Identity Authentication) to establish an interface for all your cloud systems.
The path to the cloud is also mapped out in identity and access management. However, not all companies are yet following this trend at the speed that software manufacturers hope for. In reality, hybrid scenarios predominate, bringing with them completely new challenges in the management and distribution of roles and digital identities.
Today, hybrid often means that complex workflows in SAP Identity Management are handled on-premise and transferred to the cloud via various interfaces.

SAP Identity Management focuses on the traceable management and consistent distribution of digital identities throughout their lifecycle – assignment, repeated adjustments, deletion.

SAP Access Control is a product for identifying risks, minimizing risks, and automating workflows. The focus is on the traceable management and consistent distribution of users and authorizations throughout their lifecycle.

SAP Single Sign-On enables end-to-end authentication against SAP and non-SAP applications. Central management of access data increases security, as only one user ID is required for all applications.
Simply complete the form and submit it. We will contact you as soon as possible.